The MacMillan online dictionary defines gambit as “a series of moves that you can make at the beginning of a game of chess when you offer a piece, usually a pawn, in order to get an advantage”.
Chess is a game of strategy and conquer. The strategy of the gambit would apply to any game of strategy. In fact, confidence games run by Con Men are gambits.
The DNC hack was a gambit. The young man who was murdered was a pawn. When running a political gambit, the storyline has to be equal in magnitude to the prize sought. The only storyline of sufficient magnitude for a Homescam Security takeover control of the U.S. Elections process would be if a foreign aggressor manipulated our elections and that is precisely the gambit that is being run. How do I know?
When the DNC headquarters was supposedly hacked, they didn’t call the FBI. They called a private cyber security firm called Crowdstrike to do the forensics on the hack. NPR interviewed these “experts” and they described what they did to find the malware of the hackers. There is a video on Crowdstrike’s website where they tell the story of their company. Enough said. Through their analysis, they supposedly identified a couple of malware programs called Fancy Bear and Cozy Bear.
The national storyline for Russian intrusion in American elections was predicated upon the DNC hack – however, FBI Director James Comey admits that the FBI didn’t do the forensics on the DNC servers. They relied on the story told by the private company – presumably Crowdstrike but it may have been a second expert called into look at the server. It doesn’t matter. Comey is participating in a gambit being run by the DNC, the Department of Homescam Security, the DNI and the FBI.
If you’re interested in getting more information on this story, there is a very good article on a website called KrebsOnSecurity. He knows what he’s talking about.
In the first article about the Russian Hacking storyline, it was discovered that the Department of Homescam Security already established “best practices” which required the states to build a statewide database of voter registrations and to put that information online. It’s public information. Now, with this Russian hacking gambit and the declaration of the election system as “critical infrastructure”, it seems to this Analyst that the only purpose for doing that is for the Department of Homescam Security to centralize and take control of the voter registration databases – probably locating them in the cloud. The states would then pay for “software as a service” (SAAS) with “user access” to the information – but not control of the information.
 When the scheme for government control of everything began, it was with the bombing of the Murrah Building in Oklahoma City. At first, the designation of critical infrastructure applied to federal buildings – at least that was the way it was presented. Now, with the designation of data and a software system as “critical infrastructure” to be controlled by the “intelligence community”, it means that TIA – Total Information Awareness has become TIIC – Total Information and Infrastructure Control.
When the scheme for government control of everything began, it was with the bombing of the Murrah Building in Oklahoma City. At first, the designation of critical infrastructure applied to federal buildings – at least that was the way it was presented. Now, with the designation of data and a software system as “critical infrastructure” to be controlled by the “intelligence community”, it means that TIA – Total Information Awareness has become TIIC – Total Information and Infrastructure Control.
Keeping in mind, the nationalization of critical infrastructure, the designation of monuments using the 1906 American Antiquities Act in western states is equivalent to the designation of critical infrastructure. The designation takes control of land and resources out of state control and puts it in the hands of who? We don’t know – not really.
A few years ago, Maxine Waters let the cat out of the bag in terms of the agenda.
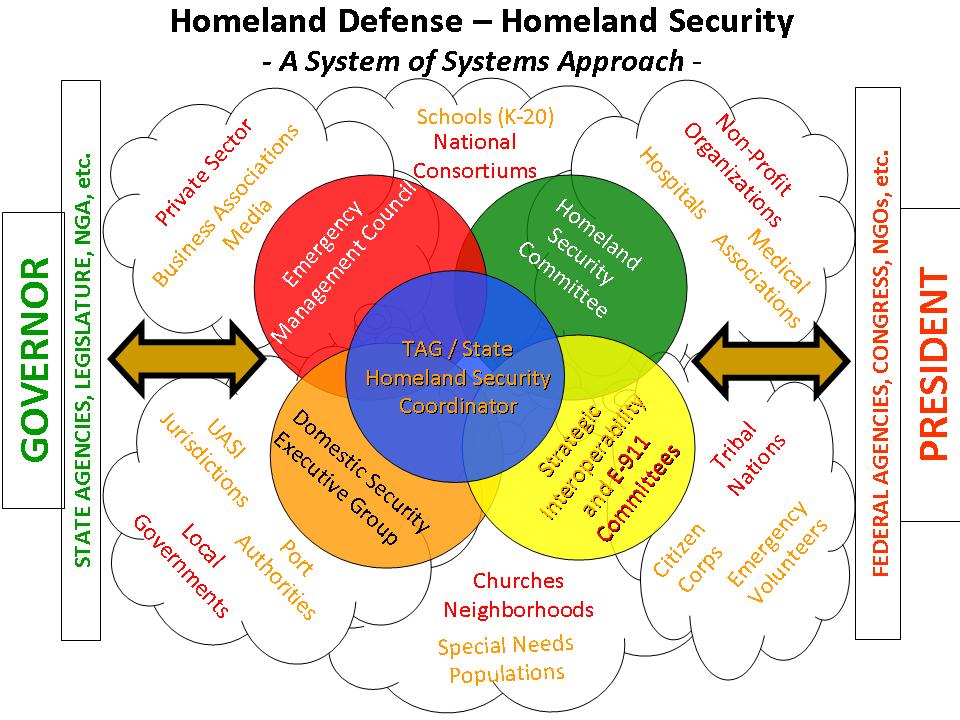
The IT systems that are designed and managed by the Director of National Intelligence, presented as being designed for “security” are an intellectual fraud. They don’t provide security for the country or it’s people. They provide the illusion of security while the country is being turned into a technological prison – a police state. This graphic was found some years ago probably on the University of Washington website but I can’t say for sure because I don’t remember:
A radical philosophy combined with corresponding changes in the management and financing of government in the 1980s and 1990s actually changed our form of government. The diagram above represents the “core” mission of government – which is security. The philosophy included implementing corporate efficiency and fee for service (user fees) – on top of existing income taxes, sales taxes, excise taxes, etc. It also included government partnering with corporations – socializing their costs while establishing systems for regulatory racketeering and vehicles to provide flows of money to corrupt politicians and their families. The racketeering, money flows and police state mechanisms ensure continued political support ![]() for the “new form” of government.
for the “new form” of government.